Continuous Trust and Runtime Authorization for Every AI Workload
As your Guardian AI Agent, Reva delivers real-time identity and adaptive trust for every AI agent to ensure governed, verifiable actions.
Risks of Uncontrolled AI Access
Traditional controls weren't built for how GenAI retrieves, reasons, and acts.
Dynamic Context & Role Changes
Agents operate with changing context, which makes static policies ineffective
Data Leakage & Unauthorized Access
Confidential & sensitive data can be exposed if access controls aren't enforced.
Lack of Permissions-Aware Retrieval
Most vector stores don't natively support granular access controls, leading to overexposure.
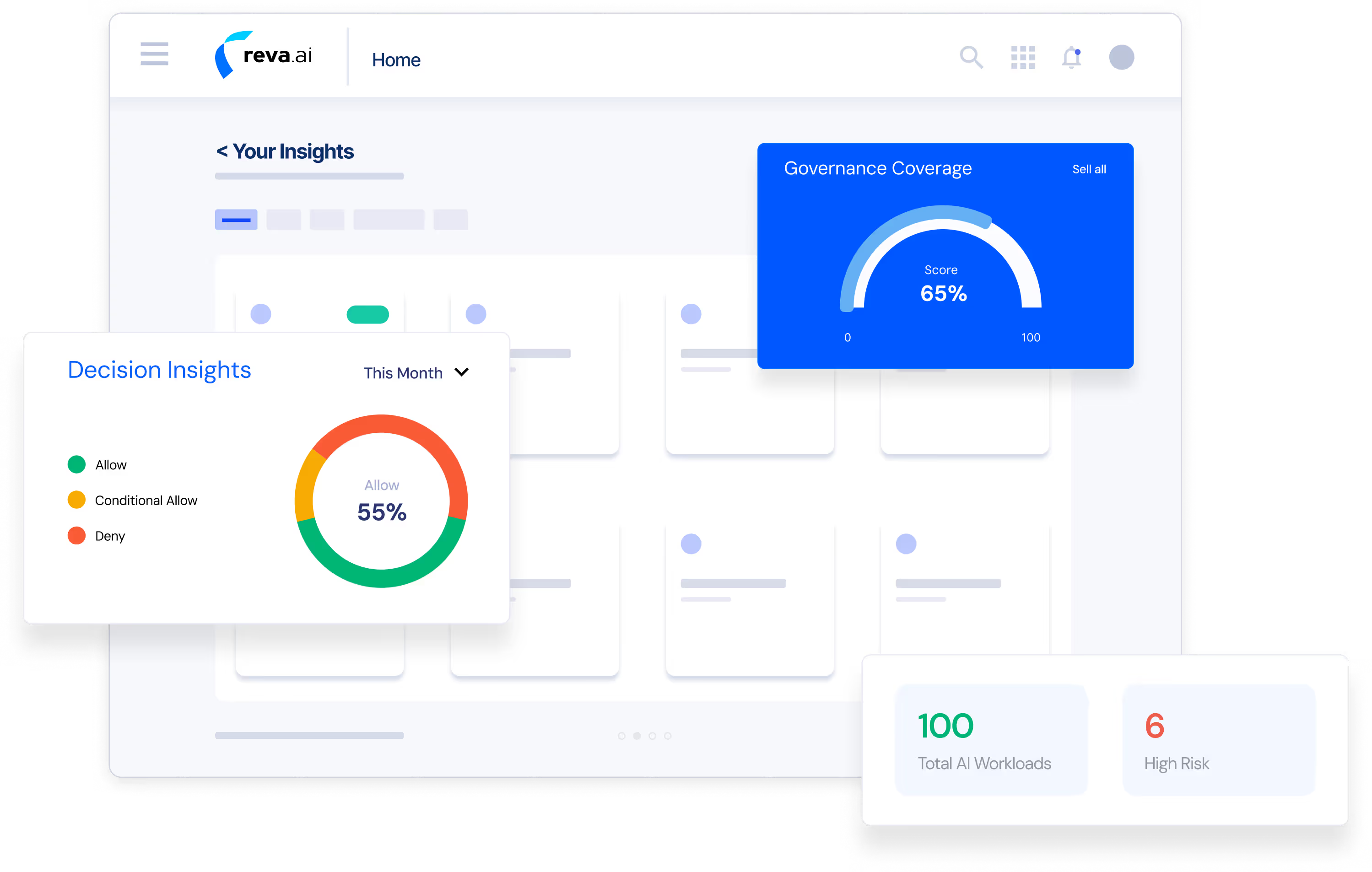
Unified AI Security & Authorization
Discover and map all AI workloads across your organization—from enterprise copilots to custom agents. Reva automatically identifies ungoverned AI systems, builds comprehensive access maps, and provides deep visibility into who has access to which agents, tools, and data.
Shadow AI Discovery & Access Visibility
Discover and map all AI workloads across your organization—from enterprise copilots to custom agents. Reva automatically identifies ungoverned AI systems, builds comprehensive access maps, and provides deep visibility into who has access to which agents, tools, and data.
Auto-Discovery: Automatically discover AI workloads across platforms (AWS Bedrock, LangChain, MCP, internal systems) without manual configuration
Intelligent Classification: Auto-classify workloads and recommend policies based on risk profile and compliance requirements
Access Explorer: Interactive visualization of agent permissions, delegation chains, and cross-application relationships
.avif)
Designing and Governing AI Policies
Reva transforms complex AI governance into a streamlined process, enabling your team to secure models, data, and agent interactions with precision and speed.

Fine-Grained Control & Global Guardrails: Design precise fine-grained policies to protect AI assets while implementing global guardrail recommendations to ensure secure operational boundaries.
Identity & Delegation Management: Secure your AI ecosystem by issuing verifiable, short-lived identities (SPIFFE/SPIRE) and designing robust delegation chains for controlled access between agents and services.
Comprehensive AI Policy Library: Accelerate adoption with a library featuring runtime guardrails mapped to critical AI threat categories (e.g., OWASP Top 10 LLM, OWASP-Agentic) and compliance frameworks (NIST AI RMF, EU AI Act).
Real-Time Policy Enforcement
Adaptive Trust Gateway provides real-time evaluation for every AI action through its integrated decision engine. Prevent drift, misuse, and emergent autonomous behavior with trust scoring and automated decision-making.
Adaptive Trust Scoring: Automatically adjust privileges based on behavior patterns and external risk signals (via CAEP and SSF) for true least privilege.
Automated Decisions: Instant allow/deny decisions and HITL orchestration for high-risk actions, preventing misuse.
Threat Prevention: Prevent drift, misuse, escalation, and emergent autonomous behavior before they impact your systems
Observability & Security Operations
Decision logs map complete agent execution paths and provide security incident kill chain visibility. Trace attacks from initial request through tool invocations to final outcome, with full audit trails for compliance and investigation.
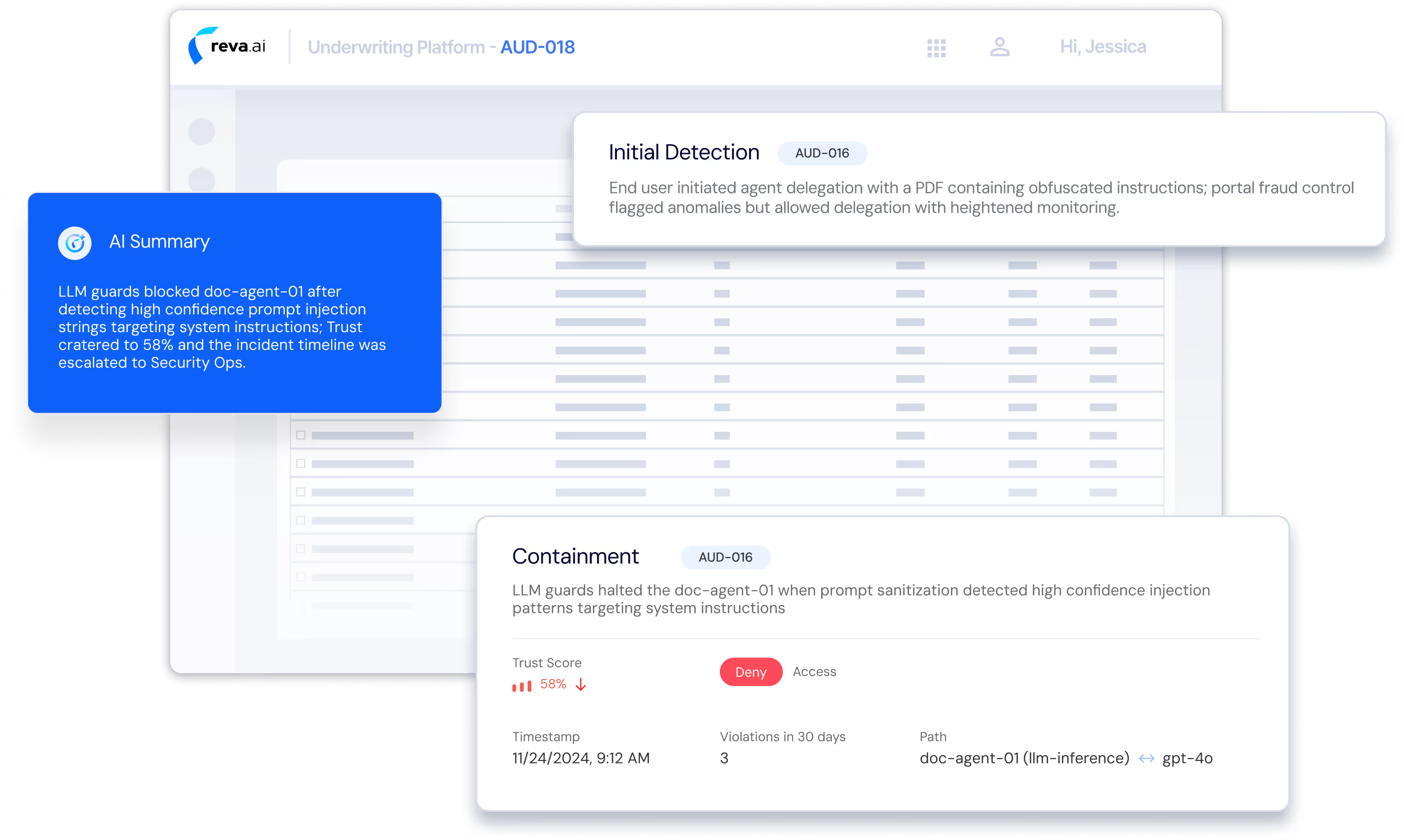
Agent Path Visibility: Decision logs map complete agent execution paths (agents -> tools -> LLM) for full operational and security traceability
Security Incident Kill Chain: Trace attacks from request through tool invocation to final outcome with full timeline reconstruction.
Behavioral Anomaly Detection: Identify unusual access patterns across agents and data to detect and contain threats before they escalate.
Securing Specific Enterprise AI Workloads
Enterprise Copilots
Secure AI Assistants
for Business Users
Protect enterprise copilots like Microsoft Copilot, Salesforce Copilot, and custom internal assistants. Reva ensures every copilot session operates with least-privilege access and full auditability.
1
Session-Based Identity: Short-lived identities for every copilot session with automatic expiration and renewal
2
Least-Privilege Policies: Context-aware policies with approval workflows that adapt to user role and data sensitivity
3
Behavioral Anomaly Detection: Identify unusual access patterns, data exfiltration attempts, and unauthorized actions in real-time
4
Full Traceability Complete audit trail for every copilot interaction, decision, and data access with compliance coverage
Coding Agents
Secure AI-Powered Development Tools
Govern coding agents like GitHub Copilot, Cursor, and custom development assistants. Reva prevents prompt injection attacks and restricts agents to safe, auditable code operations.
1
Prompt Injection Prevention: Detect and block prompt injection attacks pre-execution before they reach code repositories
2
Safe Action Enforcement: Restrict agents to safe actions with read-only code access and controlled write permissions
3
Context-Aware Rules: Repository-specific policies limiting access based on code sensitivity, branch protection, and team permissions
4
Complete Lineage: Full traceability from developer request through agent execution to code changes—developer → agent → code
RAG / Knowledge Agents
Secure Document Retrieval and Knowledge Systems
Protect RAG systems and knowledge agents that access enterprise documents, wikis, and knowledge bases. Reva ensures dynamic authorization and prevents unauthorized data access.
1
Dynamic Authorization: Context-aware authorization for document retrieval based on user role, document classification, and query intent
2
Least-Privilege Query Controls: Granular query-level controls limiting document access to only what's necessary for the specific request
3
PII and Sensitive Content Filtering: Automatic detection and filtering of PII, sensitive content, and classified information before retrieval
4
Session Isolation: Prevent context bleed between sessions and users with strict session boundaries and data isolation
MCP Servers
Unified Governance for Model Context Protocol
Govern MCP (Model Context Protocol) servers, and tools across your organization. Reva provides native enforcement and unified governance for all MCP workloads.
1
Auto-Discovery: Automatically discover MCP servers, connected agents, and available tools across your infrastructure
2
Native Tool Enforcement: Enforce policies directly at the MCP protocol level for tool invocations, parameter validation, and access control
3
Unified Governance Consistent policy enforcement and governance across all MCP workloads regardless of deployment location
4
Anomaly Detection: Identify unauthorized tool access, unusual invocation patterns, and potential security threats across MCP infrastructure
Homegrown Apps
Secure Custom AI Applications
Integrate Reva into your custom AI applications with lightweight SDKs. Externalize authorization decisions and leverage pre-built policy templates for rapid deployment.
1
Lightweight SDKs: Native SDKs for Python, Node.js, Go, and Java with minimal overhead and simple integration
2
Externalized Authorization: Centralized authorization decisions via Trust Gateway without embedding policy logic in applications
3
Pre-Built Policy Templates: Accelerate deployment with policy templates aligned with industry frameworks and best practices
4
Unified Telemetry: Consistent auditability and observability across all custom applications with unified telemetry and audit trails
Ready to get started?
See how Reva secures humans and AI agents with adaptive, least-privilege access.
Oops! Something went wrong while submitting the form.
