The Foundation of Secure, Compliant Applications
Apply consistent, policy-driven authorization across cloud-native and SaaS applications to strengthen security, reduce risk, and ensure every access decision is governed with precision.
Broken Access Control: Your Invisible Risk Multiplier
When authorization logic is custom-built and scattered across individual applications, it creates a patchwork of inconsistent rules, hidden logic paths, and fragile enforcement.
The #1
Security Risk
Broken Access Control remains the biggest threat (A01:2025) in the OWASP Top 10, driven by inconsistent authorization and missing enforcement layers.
Static Models
Don't Scale
Traditional RBAC and other static models are difficult to scale and cannot adapt to fast-changing applications or regulatory demands.
Stop Rebuilding Authorization
87% of application developers build their own authorization logic - creating duplication, technical debt, and long-term maintenance risk.
Build Cloud-Native Applications Faster
AI-powered policy design and governance help you deliver secure applications quickly using
Cedar, Amazon Verified Permissions (AVP), or OPA without deep specialization.
Maximize Engineering Velocity
Eliminate the technical debt of custom authorization. Reclaim developer time to focus on core product innovation, not security plumbing
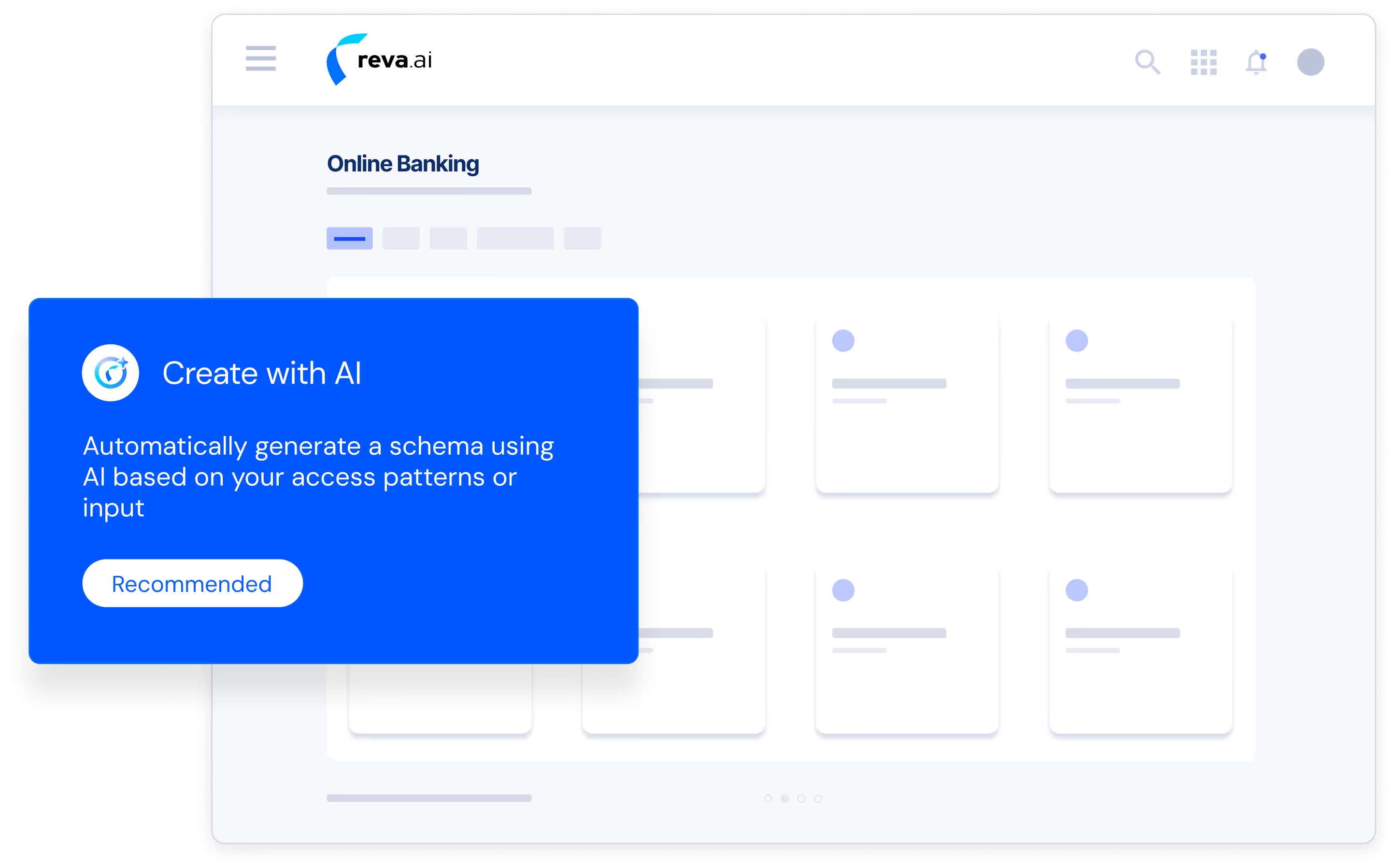
Policy Automation: Automate authorization schema generation directly from requirements, design documents, or API specifications
AI-Driven Governance: Receive AI-driven policy recommendations and conformance checks to enforce best practices and security standards automatically
Shift-Left Security: Detect risky patterns and misconfigurations early, ensuring policies are secure and correct before they reach production
Flexible, Production-Ready Enforcement
Ensure consistent and highly-available access decisions across every application and service, regardless of your stack

Universal SDKs: Deploy authorization quickly and reliably with lightweight, dedicated Enforcement SDKs available across all major development languages
Decoupled Decisioning: Maintain full flexibility with pluggable decision engines, including AVP, Cedar, or OPA - guaranteeing no lock-in and no costly rewrites
Real-Time Optimization: Leverage real-time decision logs and production data feeds to continuously fine-tune policies and enable smarter, adaptive access control
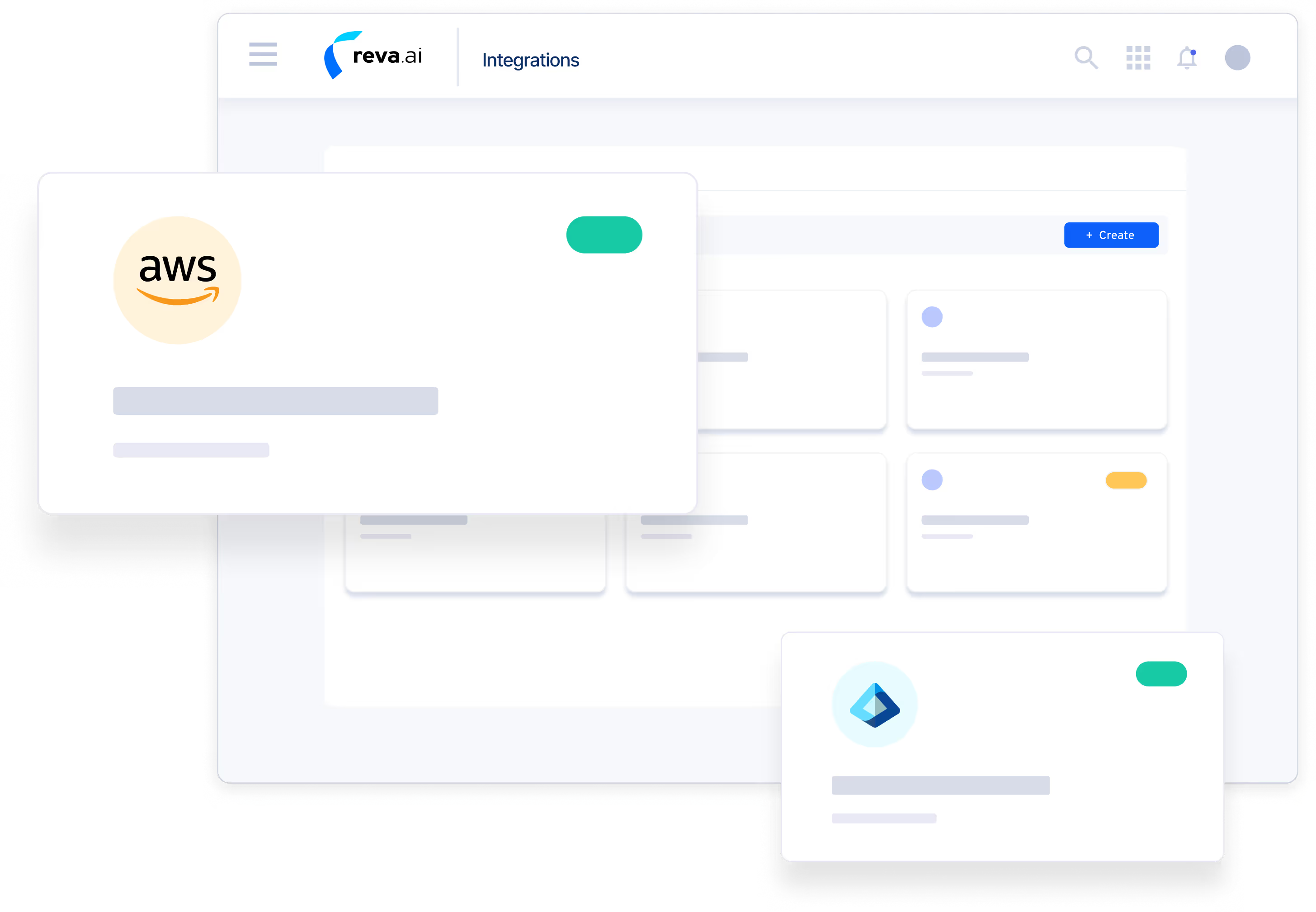
Accelerate Data Availability for Authorization
Reva ensures the decision engine gets the right data - fast and securely - by unifying data access.
Seamless Integration: Utilize pre-built integrations with leading Identity and Data providers and easily connect your applications using event-driven architecture and developer-friendly SDKs
Maximum Performance: Ensure blazing-fast authorization decisions with data caching support to avoid high-latency, real-time queries
Unlock Advanced Insights: Leverage data feeds to continuously fine-tune policies and gain deep visibility into access permissions and their precise reasoning using Access Explorer
Control and Compliance for SaaS Apps
Gain centralized visibility, map complex native authorization model, and ensure continuous policy certification across all your mission-critical SaaS applications.
Discover Policies and Visualize SaaS Access
Quickly understand and translate the complex, built-in authorization structures of your SaaS applications into centralized, governable policies.
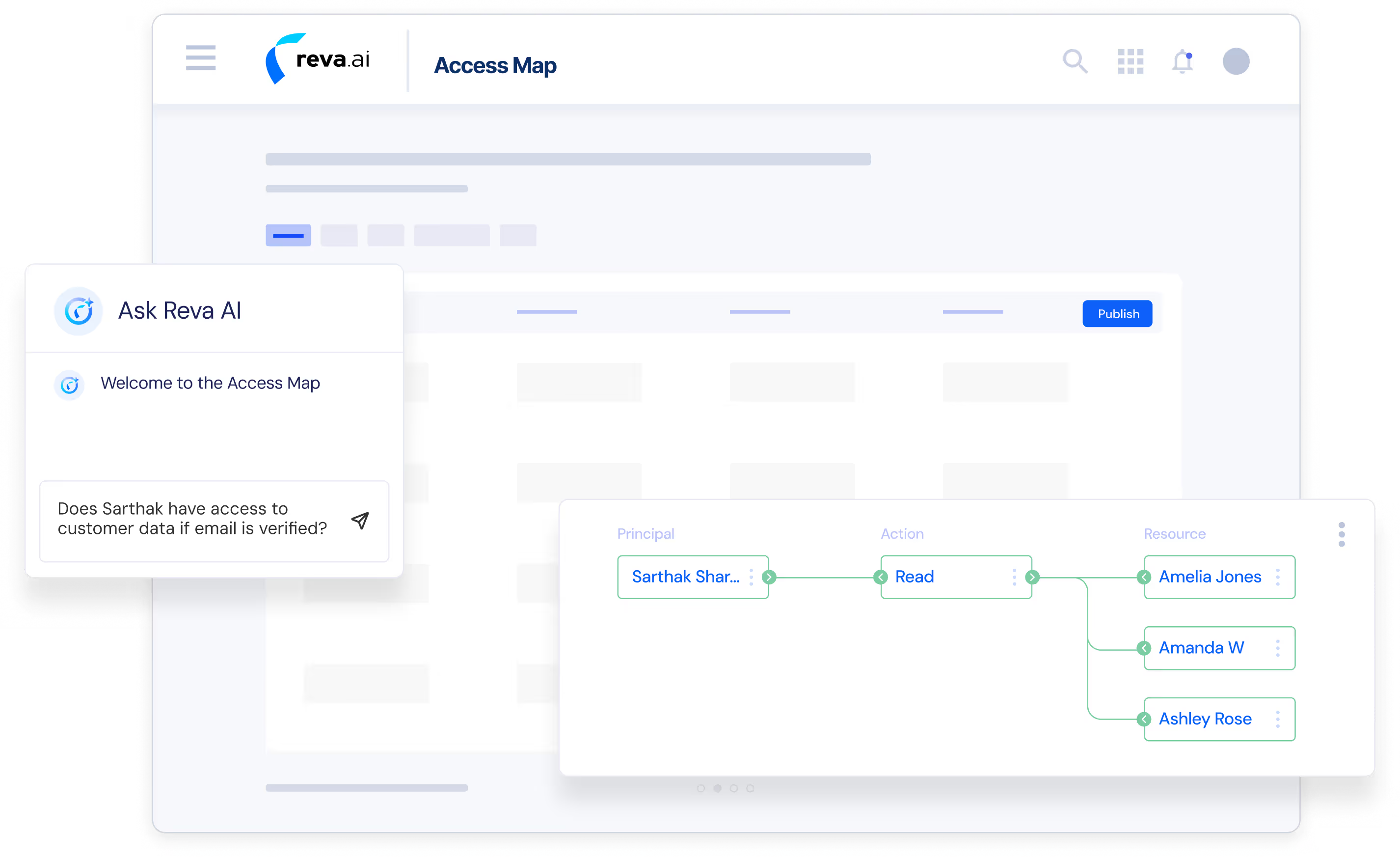
Policy Discovery & Mapping: Automatically ingest, analyze, and map the native access models and permissions of SaaS applications into a standardized, unified authorization policy model.
Complete Access Graph: Visualize relationships between users, groups, and permissions across your entire SaaS estate to easily audit access and identify excessive privileges.
Continuous Policy Certification
Ensure that all access policies meet both internal security standards and external regulatory mandates through automated validation.
Certify Policy Logic: Eliminate manual user access reviews by certifying the policy logic itself, drastically reducing audit overhead and ensuring continuous governance.
Compliance Readiness: Generate detailed, auditable reports demonstrating policy compliance with frameworks like SOC 2, HIPAA, or GDPR required for governance and certification.

Ready to get started?
See how Reva secures humans and AI agents with adaptive, least-privilege access.
Oops! Something went wrong while submitting the form.
