Enterprises have mastered the "front door" controlling who logs into their systems. But once that door is open, control often vanishes.
Traditional access control focused on authentication and static permissions. These systems answered who a user is. But in a world of multi-cloud architectures and AI-driven agents, static roles are no longer enough. Access must now adapt to context, risk, and intent in real-time.
The risks of inadequate authorization are well documented. The OWASP Top 10 consistently ranks Broken Access Control as the number one application security risk.
This shift marks the beginning of a new chapter in security: the Runtime Authorization Era.
What is Runtime Authorization
Runtime authorization means making real-time, context-aware access decisions at the moment a user, service, or machine performs an action.
Instead of using hard-coded checks or pre-computed roles, runtime authorization evaluates policies, context, and environment data dynamically every single time.
In simple terms:
- Authentication answers: Who are you?
- Runtime Authorization answers: What are you allowed to do right now, and why?
This distinction aligns with modern Zero Trust guidance from NIST, which emphasizes continuous evaluation of access decisions based on context and policy NIST Zero Trust Architecture (SP 800-207)
This is not just a technology change. It is a shift in control, from static enforcement to dynamic, explainable, and continuously governed access.
Why Static Models Fall Short
Traditional models struggle in dynamic environments:
- RBAC (Role-Based Access Control): Rigid role hierarchies lead to over-provisioned access and weak least-privilege enforcement.
- ABAC (Attribute-Based Access Control): Flexible but difficult to maintain without strong visibility and real-time context.
- Hard-coded logic: Difficult to audit, reuse, or explain across applications and services.
- They cannot adapt to the dynamic conditions of cloud-native or AI-based systems.
Static models fail to answer:
- Can this user access a dataset if they are connecting from a restricted region?
- Can this AI agent retrieve a document if the owner revoked consent recently?
- Should this service call be allowed if the upstream risk score has changed?
These are runtime questions, and static policy frameworks cannot respond to them effectively.
To move forward, organizations need policies that are written as code, reason with live context, and can be enforced dynamically at runtime.
The Convergence of Policy as Code and Real-Time Context
Policy as Code (PaC) has transformed how authorization is designed and managed.
By expressing policies in code through languages such as Cedar, Rego, or Reva’s unified schema, teams gain version control, automation, and auditability.
The next step in this evolution is combining Policy as Code with real-time context:
- Policy Information Point (PIP): Ingests environment data from systems like HR, CRM, or Cloud Config.
- Policy Decision Point (PDP): Evaluates policies dynamically for each request.
- Enforcement Layer: Executes the decision instantly through APIs, SDKs, or sidecars.
This architecture enables what Reva calls runtime governance, where policy, context, and action operate together continuously.
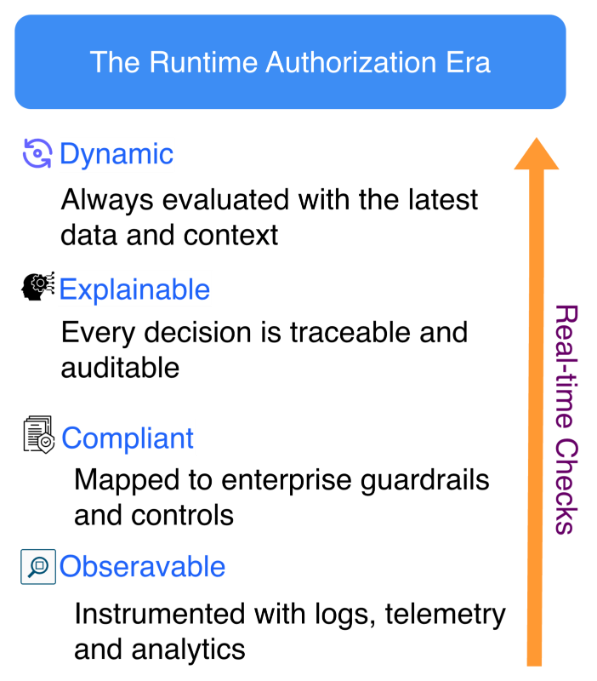
The Runtime Authorization Era
Runtime authorization creates a new control layer that unifies identity, access, and governance.
It ensures that access decisions are:
- Dynamic: Evaluated with current context and data.
- Explainable: Every decision can be traced and audited.
- Compliant: Mapped to enterprise guardrails and standards.
- Observable: Connected to logs, telemetry, and analytics.
As organizations adopt AI agents, autonomous workflows, and microservices, runtime authorization becomes essential for ensuring trust and control.
Why Reva Leads the Runtime Authorization Era
Reva was purpose-built to operate as this runtime control layer. It provides a unified Policy as Code platform that connects identity, data, and applications through real-time authorization and governance.
1. Discover: Context at Scale
Reva’s Policy Information Point (PIP) ingests contextual data from identity providers, HR systems, and application metadata through SCIM, REST, or gRPC.
This ensures that every authorization decision has complete visibility into who, what, where, and when.
Example: A user’s department, region, and clearance level are updated before each access request. Policies always use the latest information, improving both accuracy and security.
2. Enforce: Unified Policy Execution
Reva’s Policy Decision Point (PDP) executes policies written in Cedar, OPA, or Reva’s schema format.
It integrates with Amazon Verified Permissions or Cedar-based systems, Rego-based systems, or custom applications to deliver secure, low-latency, and multi-region enforcement.
Example: A financial service can evaluate a transfer request based on the manager’s clearance level, transaction amount, and time of day, all within one auditable decision.
3. Observe: Continuous Governance
Reva’s Guardrails and Access Graph bring visibility to runtime authorization.
They visualize access relationships, detect misconfigurations, and simulate the effects of policy changes before they are deployed.
Each decision can be mapped to compliance frameworks such as NIST, PCI DSS, or SOX.
Example: Detect when a policy unintentionally grants excessive privileges and simulate the correction before enforcement.
The Reva Advantage
Reva is not just a policy engine. It is a trust fabric that connects policy design, enforcement, and governance across the enterprise.
- Multi-model support:
Works with RBAC, ABAC, and ReBAC within a single, unified policy framework.
- Cross-PDP orchestration:
Integrates seamlessly with Cedar, OPA, and AVP for hybrid and multi-cloud environments.
- Runtime visibility:
Provides complete decision traceability and insight through Access Graph and Guardrails.
- AI-assisted authoring:
Automatically generates and validates policies, accelerating policy adoption and reducing errors.
- Governance alignment:
The guardrails mapped to key compliance standards such as NIST, PCI DSS, and ISO 27001.
By combining discoverability, enforcement, and observability, Reva turns authorization into an enterprise-wide control plane.
The Road Ahead: From Access to Trust
As AI systems, autonomous agents, and fine-grained services become standard, runtime authorization will define how trust is built and maintained.
Static access models cannot evaluate intent or contextual risk, but runtime authorization can.
The next steps are clear:
- AI and Authorization: Using AI to reason over context, anomalies, intent, and authorization decisions.
- Policy Lifecycle Automation: Simplifying authoring, testing, and enforcement across systems.
- Universal Runtime Control: Creating a single layer of trust across cloud, data, and AI platforms.
Reva is leading this transition by enabling every enterprise to make authorization decisions explainable, auditable, and governed.
Conclusion
The Runtime Authorization Era has begun.
It replaces static access models with dynamic, contextual, and governed authorization.
Reva stands at the center of this transformation, providing a unified control fabric for policy, data, and governance.
Reva: The Runtime Authorization Fabric for the Cloud-Native and AI-Powered Enterprise.
Request a Reva demo to see runtime authorization in action.