Continuous Trust and Runtime Authorization for Every AI Workload
As your Guardian AI Agent, Reva delivers real-time identity and adaptive trust for every AI agent - ensuring actions remain governed, verifiable, and compliant.
.webp)
The Security Gap in Agentic AI
As enterprises move from chatbots to autonomous agents, traditional IAM breaks down. Static identities and permissions cannot govern agents that change context, chain actions, and access data and tools dynamically. Agentic AI introduces new risks - privilege drift, data leakage, prompt injection, and opaque decision paths - that existing security models were not designed to handle.
Dynamic Context & Role Drift
Agents operate with shifting intent and execution context, making static roles and pre-defined permissions ineffective.
Data Leakage & Unauthorized Access
Without runtime authorization, agents can overreach - accessing or exposing sensitive data beyond policy or user intent.
Permissions-Unaware Retrieval
Most RAG pipelines and vector stores lack identity-aware controls, leading to over-retrieval and unintended data exposure.
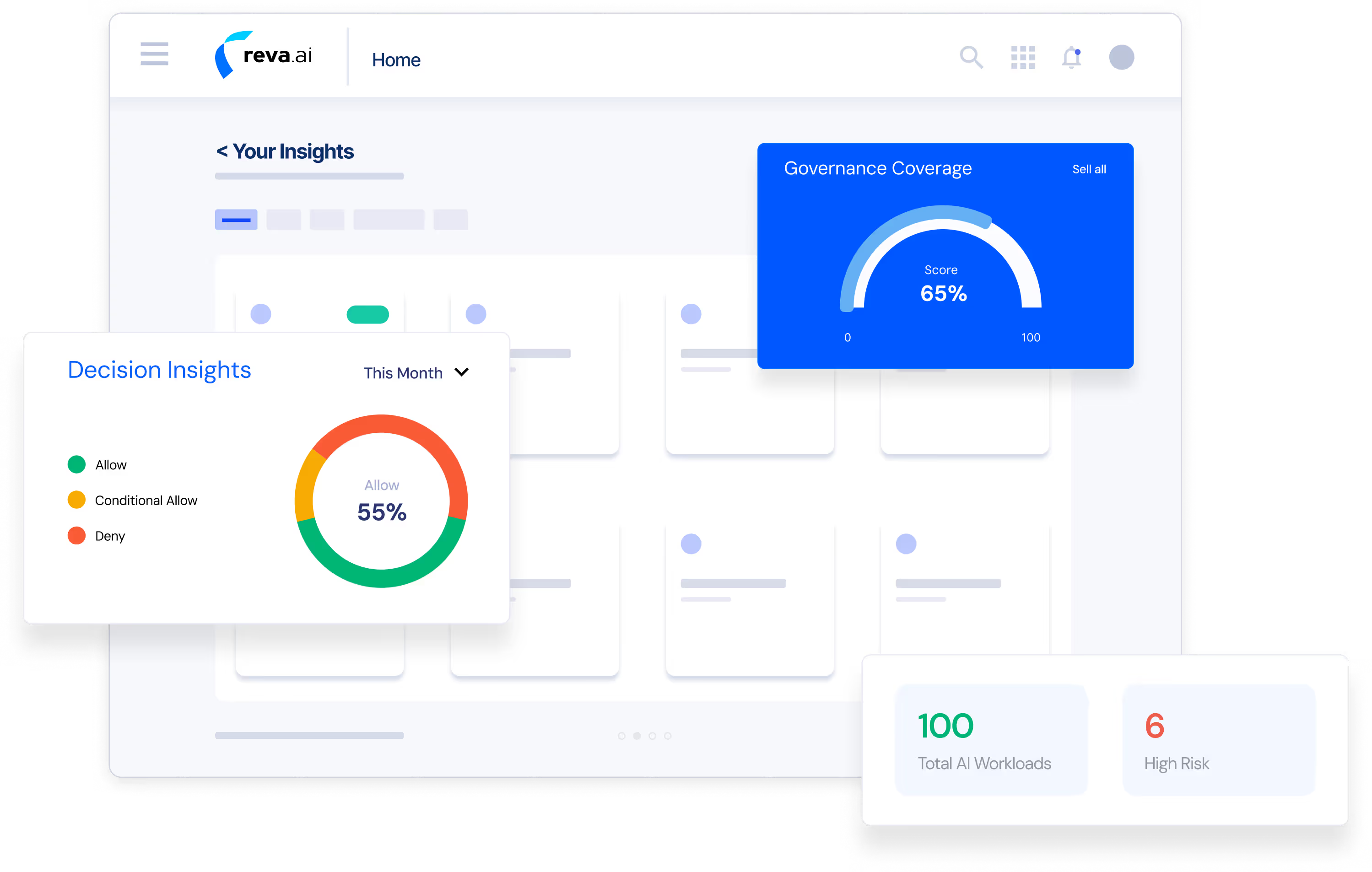
Unified AI Security & Authorization
Reva is an autonomous AI security and authorization platform that delivers end-to-end governance - from discovery through runtime enforcement. It continuously evaluates agent behavior, and actions in real time, incorporating external risk signals (via CAEP and SSF) to strengthen decisions and enforce guardrails aligned with industry frameworks.
Shadow AI Discovery & Access Visibility
Reva automatically identifies ungoverned AI systems, builds comprehensive access maps, and provides deep visibility into who has access to which agents, tools, and data.
Auto-Discovery: Automatically discover AI agents and workloads across platforms including AWS Bedrock, LangChain, n8n, MCP, and internal systems
Intelligent Classification: Auto-classify workloads and recommend policies based on risk profile and compliance requirements
Access Explorer: Interactive visualization of agent permissions, delegation chains, and cross-application relationships
.avif)
Designing and Governing AI Policies
Reva transforms complex AI governance into a streamlined process, enabling your team to secure models, data, and agent interactions with precision and speed.

Granular Access Control & Guardrails: Design fine-grained authorization policies and apply guardrails to enforce secure operational boundaries
Identity & Delegation Management: Issue verifiable, short-lived identities (SPIFFE/SPIRE) and define controlled delegation paths between agents and tools
Comprehensive AI Policy Library: Accelerate adoption with runtime guardrails mapped to critical AI threat categories (OWASP Top 10 LLM, OWASP Agentic) and compliance frameworks (NIST AI RMF, EU AI Act)
Real-Time Policy Enforcement
The Reva Trust Gateway evaluates every AI action at runtime through an integrated decision engine—preventing drift, misuse, and emergent autonomous behavior.
Adaptive Trust Scoring: Dynamically adjust privileges based on behavior patterns and external risk signals (CAEP, SSF)
Automated Decisions: Instant allow/deny decisions with human-in-the-loop orchestration for high-risk actions
Threat Prevention: Stop privilege escalation, misuse,
and unintended agent behavior before impact
Observability & Security Operations
Reva provides forensic-grade visibility into agent execution
and security incidents—supporting audit, investigation, and response.
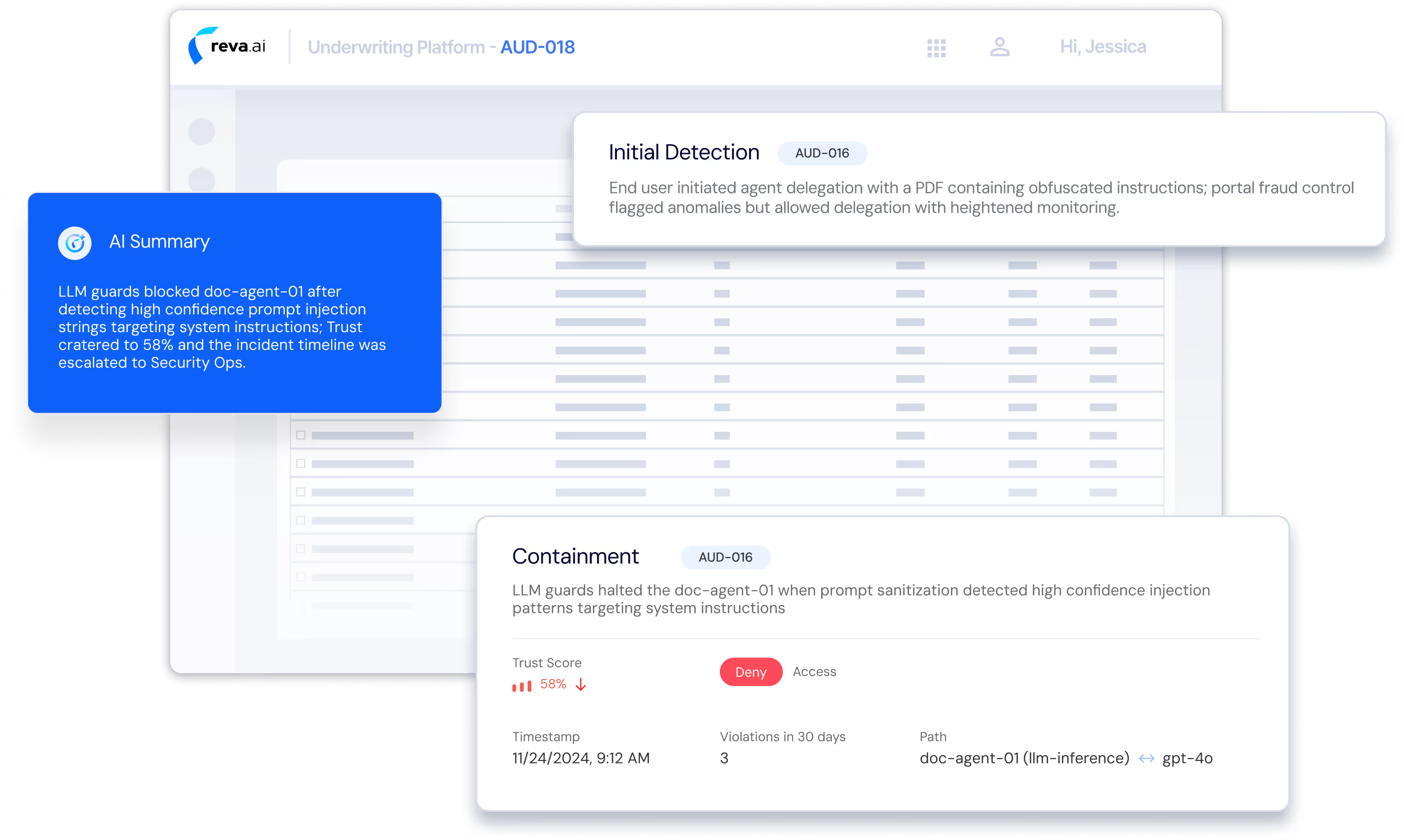
Agent Path Visibility: Decision logs capture complete execution paths (agent → tool → LLM) for full traceability
Security Incident Kill Chain: Reconstruct attacks from initial request through tool invocation to final outcome
Behavioral Anomaly Detection: Detect unusual access patterns across agents and data to contain threats early
Ready to get started?
See how Reva secures humans and AI agents with adaptive, least-privilege access.
Oops! Something went wrong while submitting the form.