Runtime Authorization & Security for MCP Servers
Enforce real-time, policy-driven control over every tool invocation — no agent rewrites, no embedded policy code.
%20(1).avif)
The Security Gap in MCP-Based Architecture
As enterprises adopt agentic AI, the Model Context Protocol (MCP) has become the standard interface for agents to invoke tools via MCP servers. But MCP defines connectivity — not security.
Without centralized runtime authorization, MCP server access defaults to static credentials, embedded logic, or coarse allowlists — resulting in inconsistent enforcement, excessive privilege, and limited visibility into agent-driven tool usage.
Without centralized runtime authorization, MCP server access defaults to static credentials, embedded logic, or coarse allowlists — resulting in inconsistent enforcement, excessive privilege, and limited visibility into agent-driven tool usage.
Uncontrolled Tool Invocation
Agents invoke sensitive tools through MCP servers without contextual, policy-driven runtime evaluation.
Broken Accountability
On-behalf-of execution chains obscure which human or system ultimately authorized a specific tool action.
Decentralized MCP Server Sprawl
MCP servers operate across VPCs, developer laptops, and SaaS environments with no shared authorization model or audit layer.
Declarative Authorization & Security for MCP Servers
Reva is the centralized authorization and runtime control plane for MCP servers and agent tool access. Through the Reva Trust Gateway, every MCP server request is evaluated in real time against granular access policies, contextual runtime guardrails, and adaptive behavioral risk signals from the Reva Policy Intelligence engine.
Eliminate Shadow MCP Servers with Automated Discovery
Reva provides continuous visibility into MCP-based tool ecosystems across hybrid environments.
MCP Discovery: Automatically identify MCP servers, connected agents, exposed tools, identities, and effective permissions by observing authorization flows and integrating with infrastructure and service registries.
MCP Access Graph (via Reva Data Fabric): Build a real-time graph of which agents can invoke which tools, through which MCP servers, under which identities and contextual attributes.
Exposure & Drift Detection: Detect orphaned MCP servers, unused tools, excessive agent permissions, standing privilege, and unauthorized deployments before they become exploitation paths.
.webp)
Runtime Authorization & Guardrails for Every MCP Server Request
Reva evaluates authorization policy, runtime guardrails, and behavioral risk together - not as separate control layers.
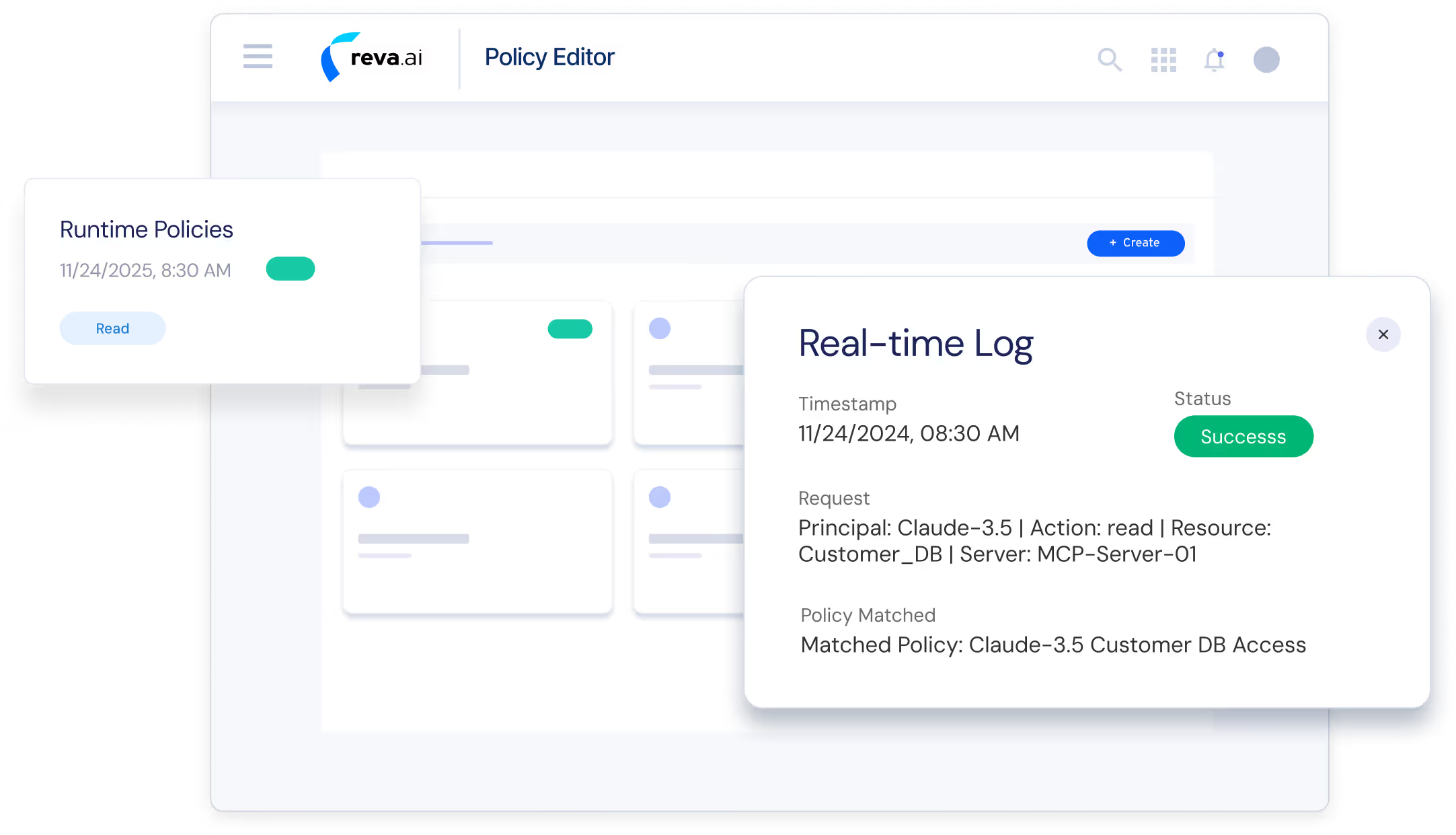
Policy-driven invocation control (Trust Gateway): MCP servers call Reva for every tool request. Reva evaluates who can invoke which tool, via which MCP server, under what identity, attributes, and environmental context.
Runtime security guardrails: Tool parameters and execution context are validated inline with authorization to prevent unsafe inputs, execution abuse, excessive agency, lateral movement, or unintended data exposure.
Verified identity & adaptive enforcement: MCP servers propagate OAuth 2.1/OIDC identities with each request. Reva continuously evaluates behavioral patterns and contextual risk signals to dynamically allow, restrict, require approval, or deny execution.
Behavioral Monitoring & Adaptive Control
Reva moves beyond static authorization by continuously assessing MCP server behavior over time.
Policy Intelligence: Analyze authorization request patterns to detect anomalous tool invocation behavior, excessive access attempts, or agent goal drift.
Adaptive response orchestration: Automatically trigger access clipping, step-up approvals, delegation controls, quarantine, or revocation — with optional human-in-the-loop workflows.
Explainable decisions: Generate decision snapshots and behavioral evidence for SOC, compliance, and audit reporting.
.png)
Ready to get started?
See how Reva secures humans and AI agents with adaptive, least-privilege access.
Oops! Something went wrong while submitting the form.